In this post, we will scan GO application code for security issues using gosec and will also integrate gosec with SonarCloud.
We will explore below topics
What is gosec?
Installing gosec
Running security checks for a GO code
Analyzing gosec reports
SonarCloud Integration with gosec
Companies using gosec
What is gosec?
gosec is a static code analyzer tool for inspecting go application code for security problems.
static code analyzer meaning - analyze code without running the application.
Gosec currently has a set of 30 rules that map to the Common Weakness Enumeration (CWE) framework. Those rules help to secure your code by covering 8 of the 2019 CWE Top 25 Most Dangerous Software Errors.
Installing gosec
gosec can be installed using go get or using CLI.
If you already have go installed then run below command to install gosec.
go get github.com/securego/gosec/cmd/gosec
After running this command, you would see gosec executable available here $GO_PATH/bin/gosec.
If you don’t have GO installed, you can install gosec using CLI.
Please have a look at gosec CLI installation options
Running security checks for a GO project
I will be using my existing go project github repo for running gosec security checks.
You could create a simple go project and execute gosec.
Running gosec from project root folder
gosec ./...
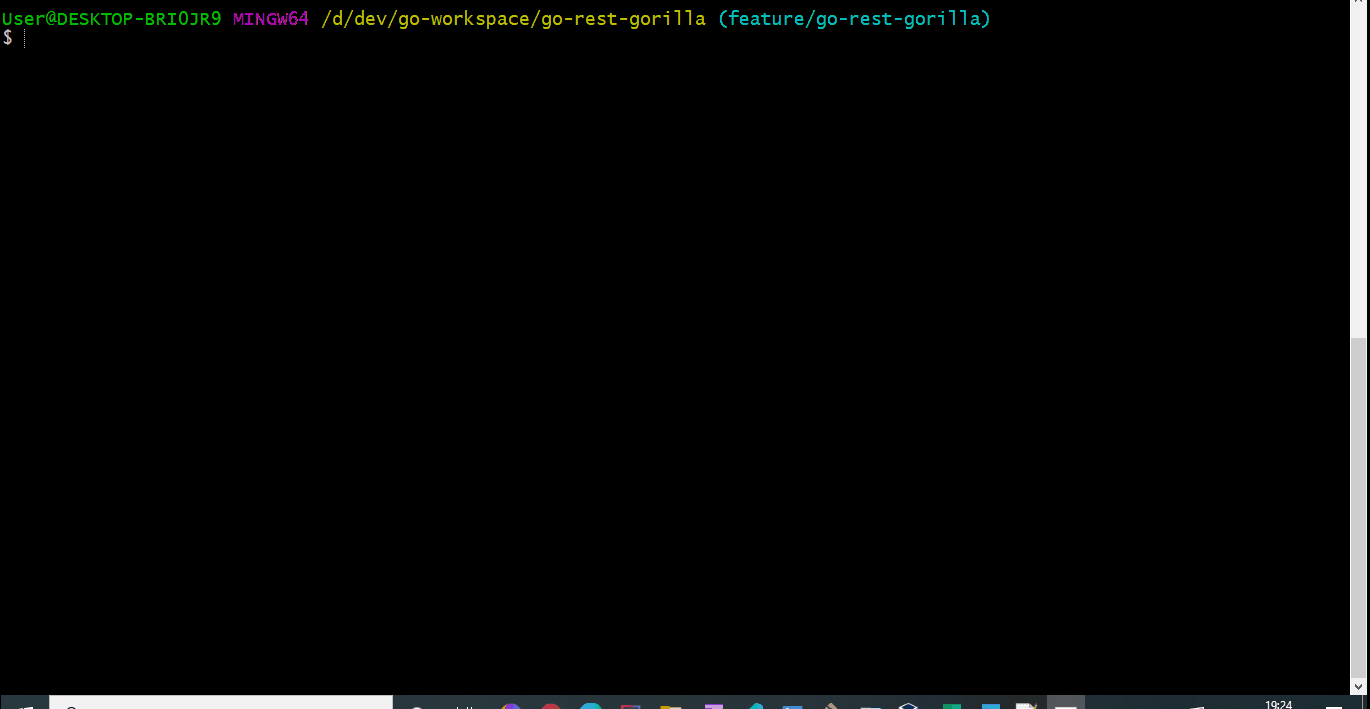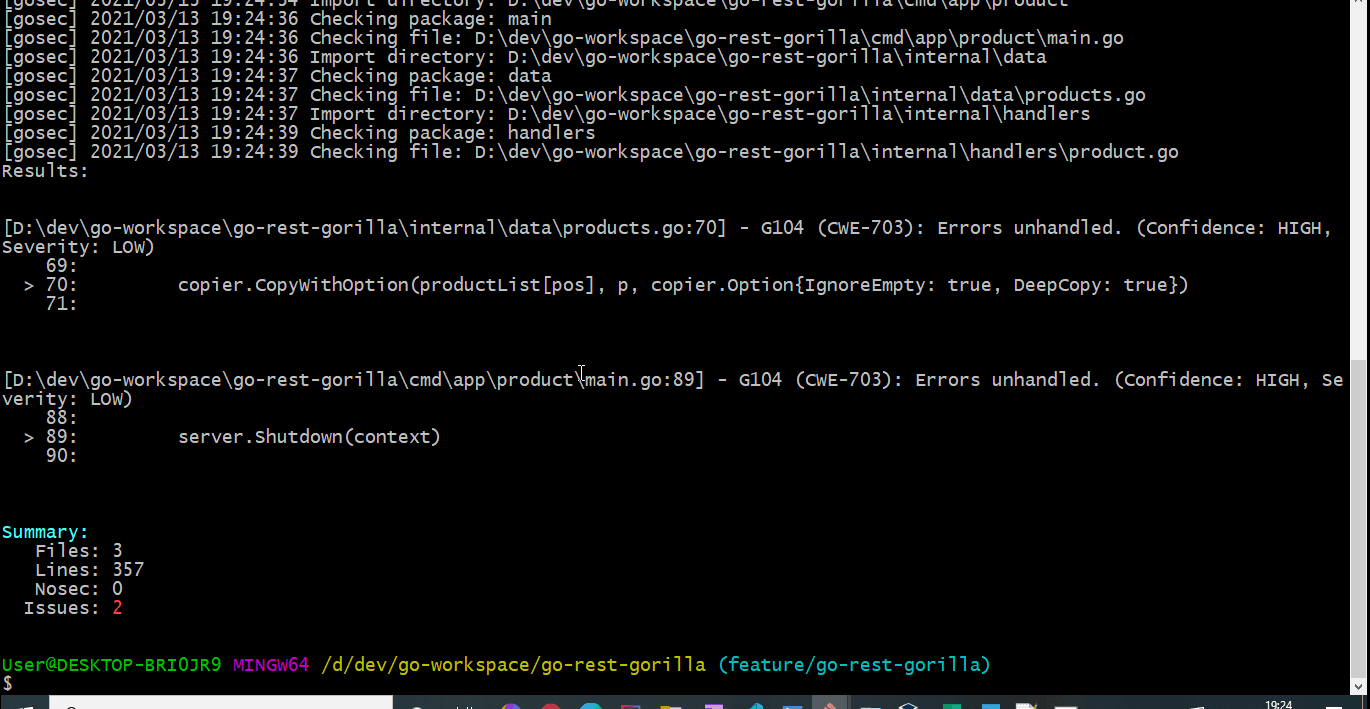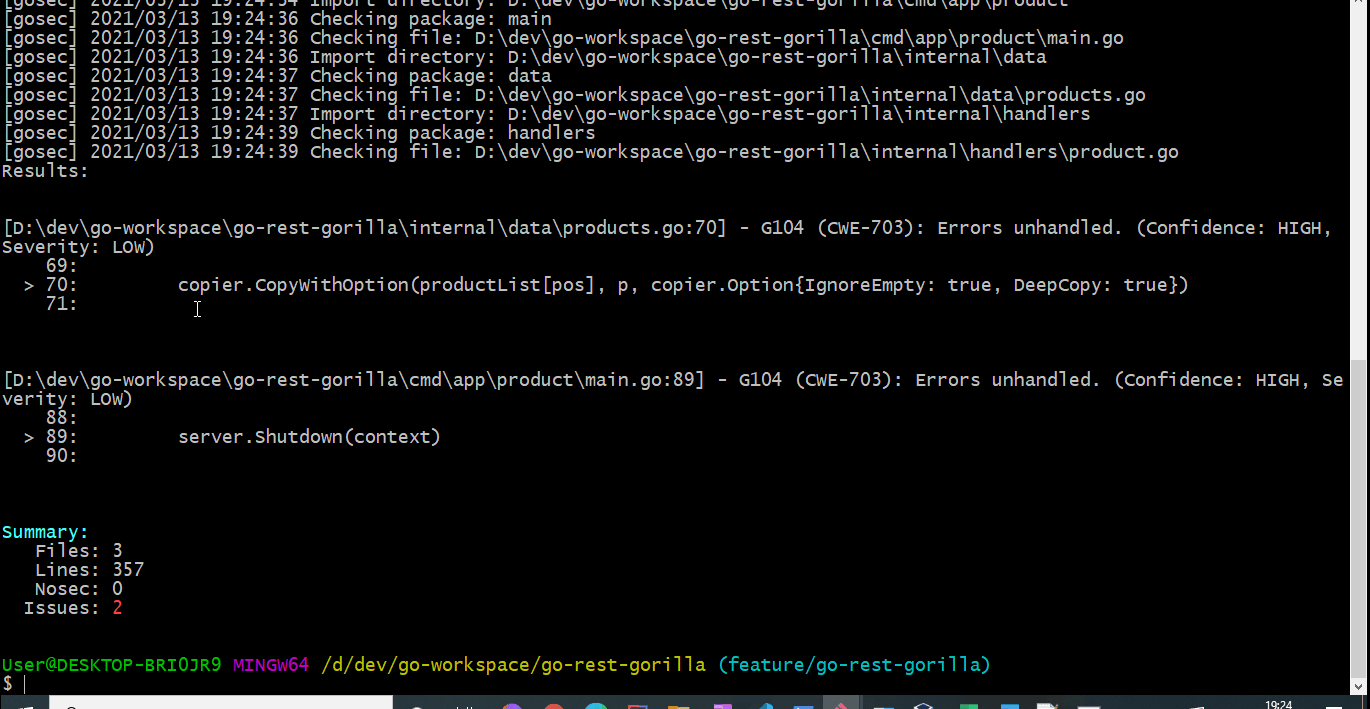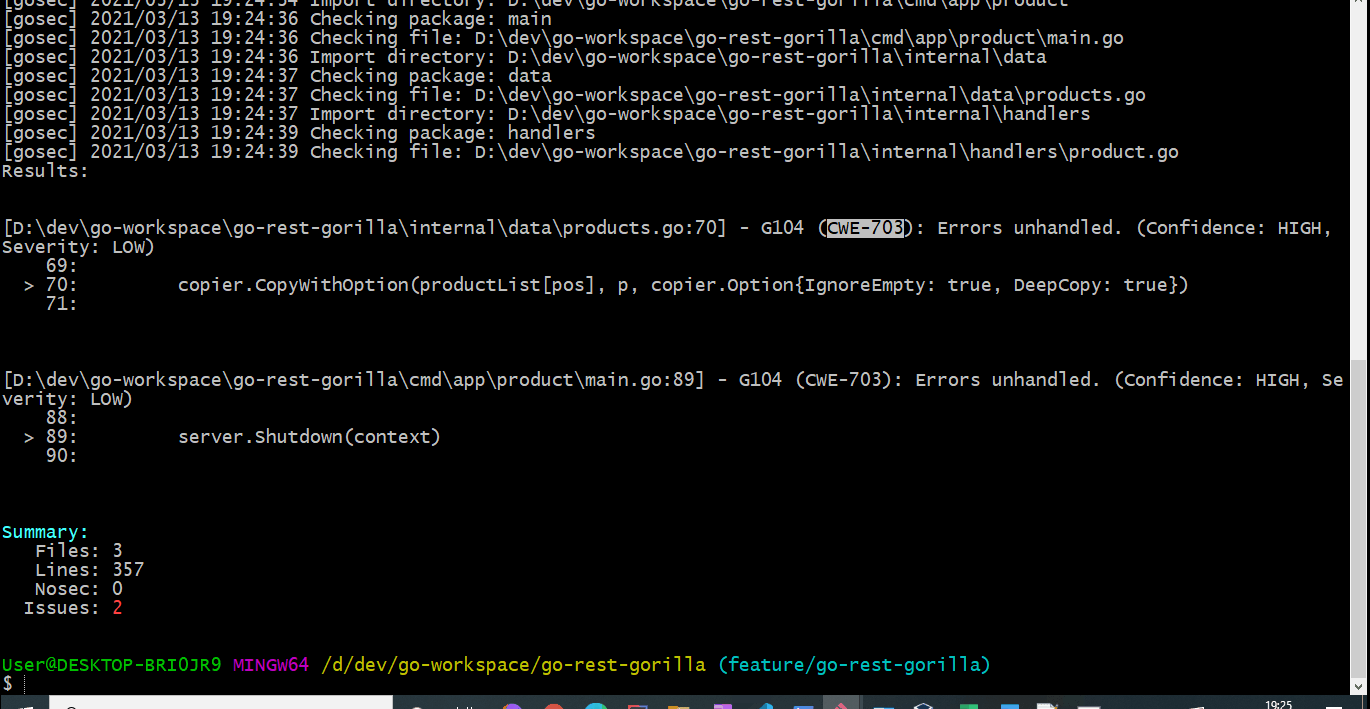
This will scan all the go files located in all the packages and sub packages from the root folder.
Analyzing reports
You can also specify security check result to be produced in a specific format and written to a file.
json example
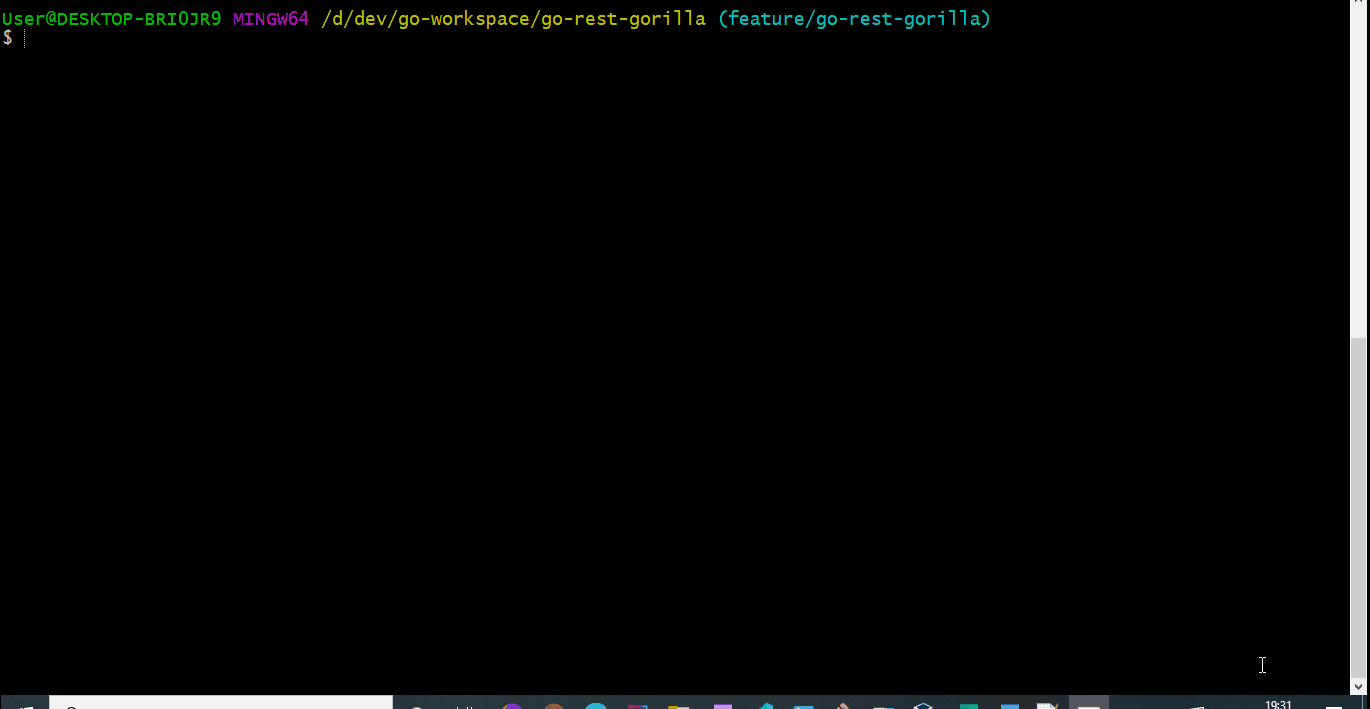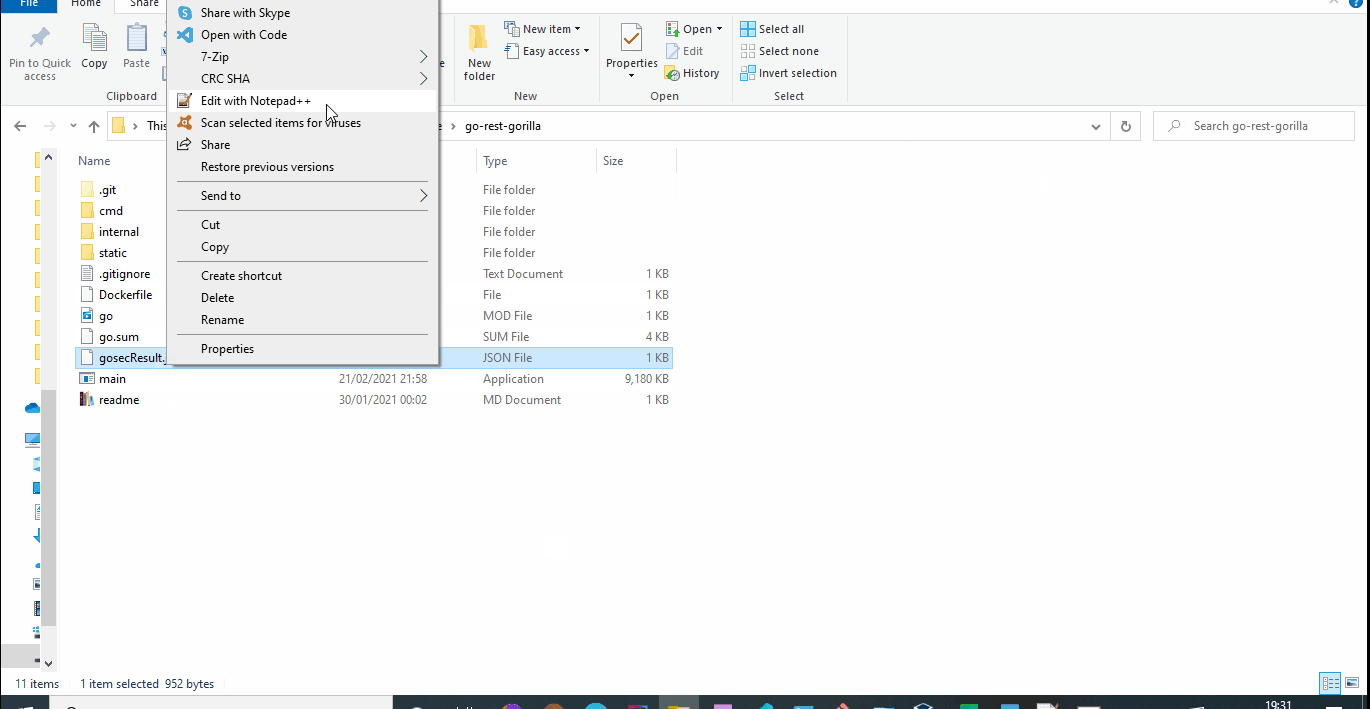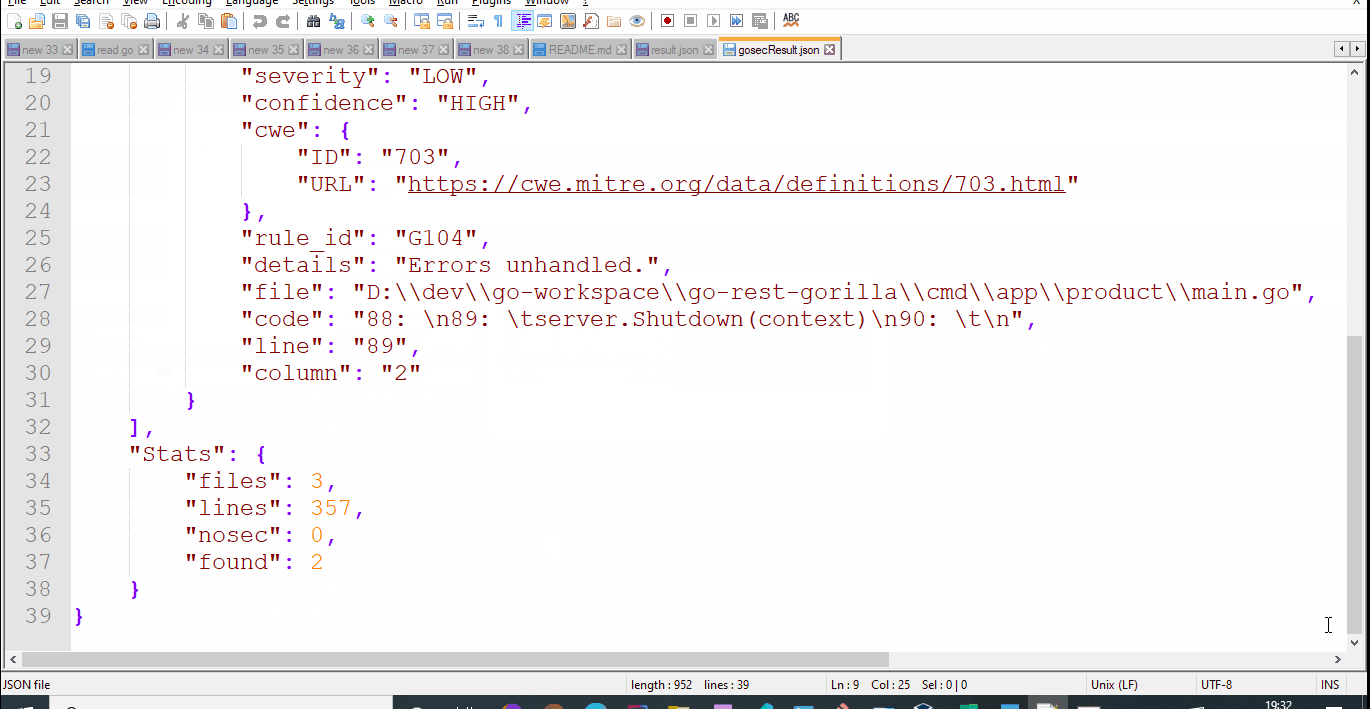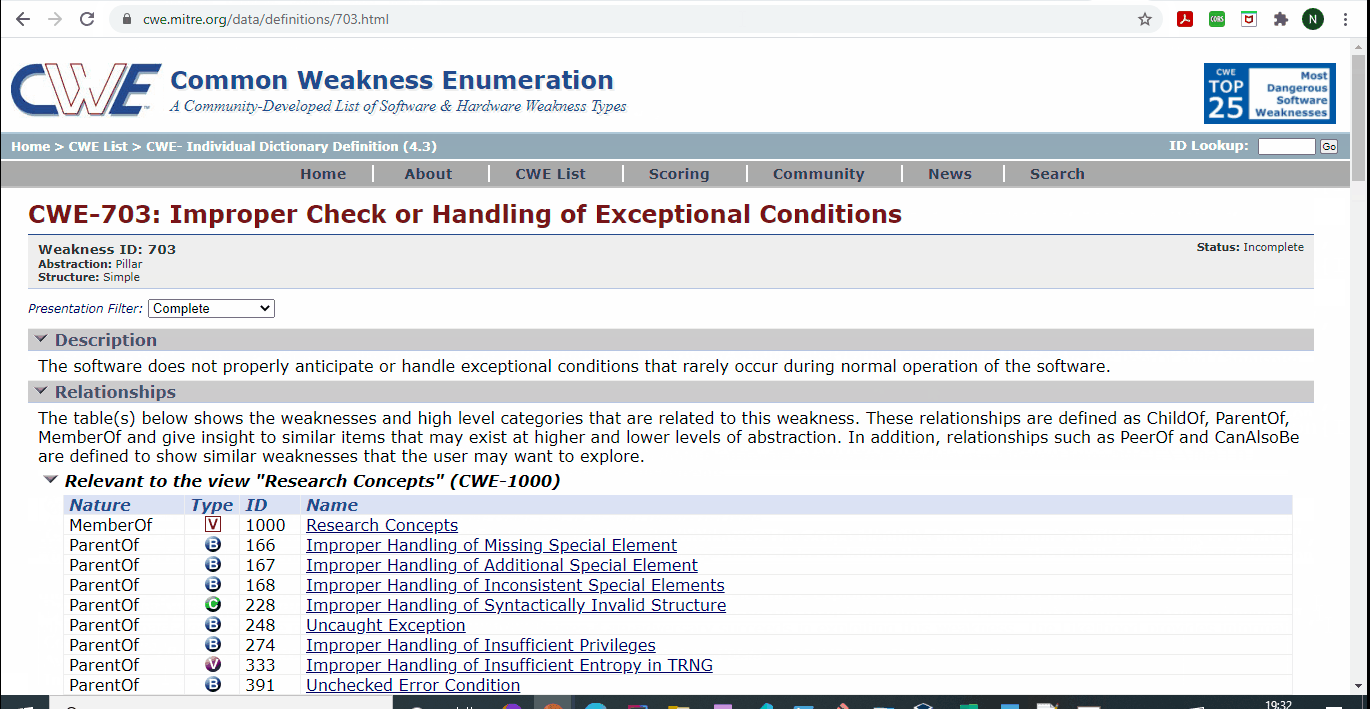
gosec -fmt=json -out=gosecResult.json ./...
This will generate security scan result in the mentioned json file.
SonarCloud Integration
gosec security result can be easily integration with SonarCloud and then we analyse result on SonarCloud.
Configuring project in SonarCloud
We will need to configure github repo in SonarCloud and for this, we will create new project in SonarCloud and link that project to github repo and branch.
Adding sonar-project.properties to the project
Few important properties
sonar.projectKey = project key of new project which we just created on the SonarCloud.
sonar.externalIssuesReportPaths = We will generate this report in sonar supported format by using gosec command.
sonar.projectKey=gosec_go-rest-api
sonar.organization=bethecodewithyou-github
sonar.host.url=https://sonarcloud.io
sonar.sources=.
sonar.exclusions=**/*_test.go
sonar.externalIssuesReportPaths=gosecReport.json
Generate gosec report for SonarCloud
gosec -fmt=sonarqube -out=gosecReport.json ./...
If you notice here, we are using sonarqube format and it is one of the supported formats in gosec.
Running the Sonar Scanner
sonar-scanner.bat \
-D"sonar.organization=bethecodewithyou-github" \
-D"sonar.projectKey=gosec_go-rest-api" \
-D"sonar.sources=." \
-D"sonar.host.url=https://sonarcloud.io"
After running this command, the results should be available on your SonarCloud server shortly.
You can take a look here on - downloading and configuring Sonar Scanner.
Analyzing gosec report on SonarCloud
Now, we will analyze gosec report directly on SonarCloud.

Companies using gosec
List of companies using gosec. Sourced from here.
- Gitlab
- CloudBees
- VMware
- Codacy
- Coinbase
- RedHat/OpenShift
- Guardalis
- 1Password
- PingCAP/tidb